{{< highlight bash >}}keytool -exportcert -keystore hadoop-server.keystore -alias foo-1.cloudera.com \
-storepass cloudera -file foo-1.cert
openssl x509 -inform der -in foo-1.cert > foo-1.pem
{{< /highlight >}}
Once you've done this for each host in the cluster, you can concatenate the .pem files into one .pem file which can serve as the Hue truststore:
{{< highlight bash >}}cat foo-1.pem foo-2.pem ... > huetrust.pem{{< /highlight >}}
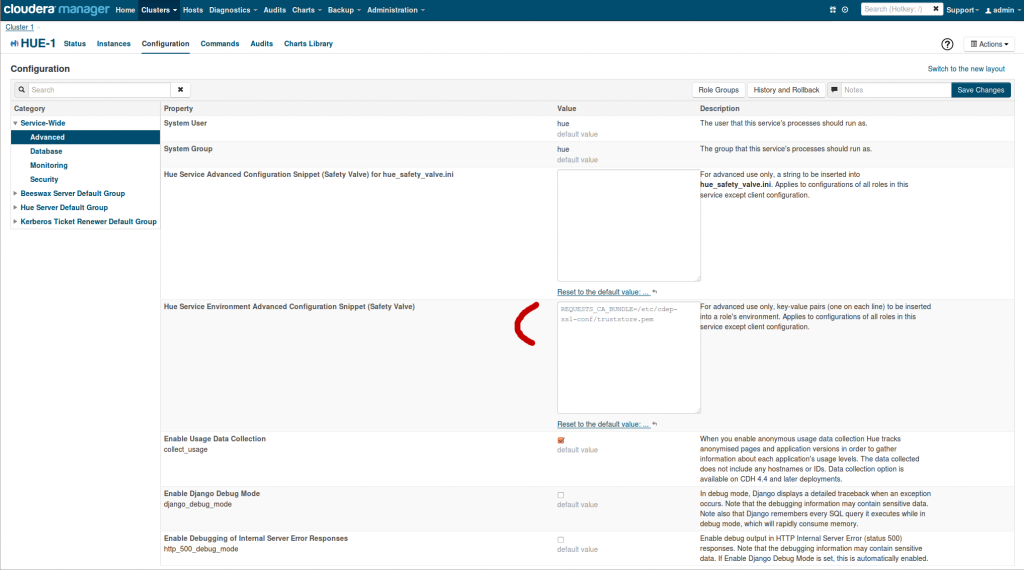
After running it, set REQUESTS_CA_BUNDLE in the Hue environment safety valve to /etc/hadoop/ssl-conf/huetrust.pem
Here is an interesting link if you want to read more about generating SSL certificates.
As usual feel free to comment and send feedback on the hue-user list or @gethue!
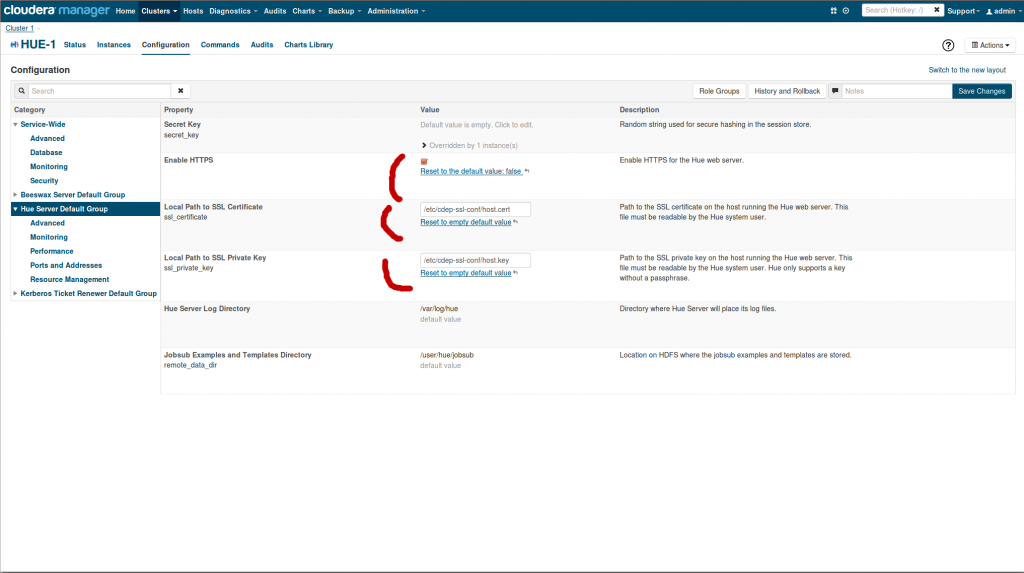 ][5]
Here is an example of creation of a certificate for enabling SSL:
{{< highlight bash >}}
[root@cehd1 hue]# pwd
/home/hue
[root@cehd1 hue]# ls
cacerts cert key
{{< /highlight >}}
Generate a private key for the server:
{{< highlight bash >}}[root@cehd1 hue]# openssl genrsa -out key/server.key 4096{{< /highlight >}}
Generate a "certificate request" for the server:
{{< highlight bash >}}[root@cehd1 hue] openssl req -new -key key/server.key -out request/server.csr{{< /highlight >}}
You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank. For some fields there will be a default value, if you enter '.', the field will be left blank.
{{< highlight bash >}}Country Name (2 letter code) [XX]:US
State or Province Name (full name) []:Colorado
Locality Name (eg, city) [Default City]:Denver
Organization Name (eg, company) [Default Company Ltd]:Cloudera
Organizational Unit Name (eg, section) []:COE
Common Name (eg, your name or your server's hostname) []:test.lab
Email Address []:
Please enter the following 'extra' attributes to be sent with your certificate request
A challenge password []: ## note this was left
An optional company name []:
{{< /highlight >}}
Self-sign the request, creating a certificate for the server:
{{< highlight bash >}}[root@cehd1 hue] openssl x509 -req -days 365 -in request/server.csr -signkey key/server.key -out cert/server.crt
Signature ok
subject=/C=US/ST=Colorado/L=
][5]
Here is an example of creation of a certificate for enabling SSL:
{{< highlight bash >}}
[root@cehd1 hue]# pwd
/home/hue
[root@cehd1 hue]# ls
cacerts cert key
{{< /highlight >}}
Generate a private key for the server:
{{< highlight bash >}}[root@cehd1 hue]# openssl genrsa -out key/server.key 4096{{< /highlight >}}
Generate a "certificate request" for the server:
{{< highlight bash >}}[root@cehd1 hue] openssl req -new -key key/server.key -out request/server.csr{{< /highlight >}}
You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank. For some fields there will be a default value, if you enter '.', the field will be left blank.
{{< highlight bash >}}Country Name (2 letter code) [XX]:US
State or Province Name (full name) []:Colorado
Locality Name (eg, city) [Default City]:Denver
Organization Name (eg, company) [Default Company Ltd]:Cloudera
Organizational Unit Name (eg, section) []:COE
Common Name (eg, your name or your server's hostname) []:test.lab
Email Address []:
Please enter the following 'extra' attributes to be sent with your certificate request
A challenge password []: ## note this was left
An optional company name []:
{{< /highlight >}}
Self-sign the request, creating a certificate for the server:
{{< highlight bash >}}[root@cehd1 hue] openssl x509 -req -days 365 -in request/server.csr -signkey key/server.key -out cert/server.crt
Signature ok
subject=/C=US/ST=Colorado/L=